Brilliant Minds
It's my firm belief that each of us possesses extraordinary gifts and talents waiting to shine. Sometimes, all it takes is to discover the hidden gem within and tirelessly polish it until it gleams like a brilliant diamond.
It's my firm belief that each of us possesses extraordinary gifts and talents waiting to shine. Sometimes, all it takes is to discover the hidden gem within and tirelessly polish it until it gleams like a brilliant diamond.
Embrace the winds of opportunity and let your dreams take flight. With determination and vision, you can reach heights you never thought possible.
Boundless possibilities await, and with each step forward, we advance toward our dreams. Let nothing deter you on this journey of ever-expanding horizons.
The compound effect is real. Putting in work over time!
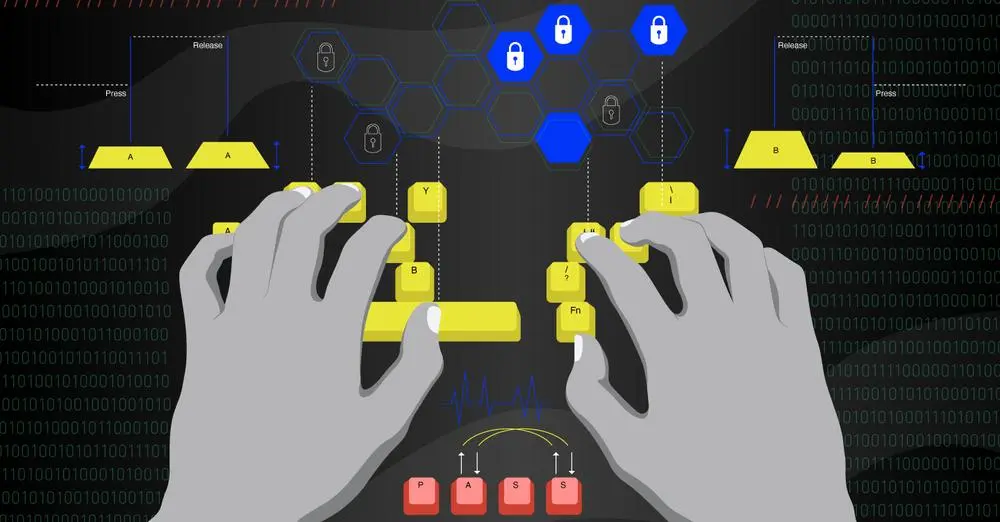
The keystroke dynamics that are used in this article’s machine learning models for user recognition are behavioral biometrics. Keystroke dynamics uses the distinctive way that each person types to confirm their identity. This is accomplished by analyzing the 2 keystroke events on Key-Press and Key-Release — that make up a keystroke on computer keyboards to extract typing patterns. The article will examine how these patterns can be applied to create 3 precise machine learning models for user recognition.
.

The keystroke dynamics that are used in this article’s machine learning models for user recognition are behavioral biometrics. Keystroke dynamics uses the distinctive way that each person types to confirm their identity. This is accomplished by analyzing the 2 keystroke events on Key-Press and Key-Release — that make up a keystroke on computer keyboards to extract typing patterns. The article will examine how these ML Models can be used in real-life situations to predict an user.

Unlock the full potential of your Raspberry Pi 4B as I guide you through transforming it into a versatile coding machine or even a web server. In this concise handbook, I'll punctually and minimalistically outline the steps to install Ubuntu Desktop, essential software, packages, and applications, while also exploring fine-tuning options. Get ready to unleash the power of your Raspberry Pi!
Discover the power of Pi-hole, your ultimate tool for reclaiming control over your internet browsing experience. In this comprehensive handbook, I'll take you through each step of the process, from understanding the basics to setting up your very own Pi-hole ad blocker.
In this tutorial, I'll show you how to create a Twitter bot that can intelligently reply to mentions. Whether you're a developer looking to explore the possibilities of automation or just curious about Twitter bots, I've got you covered.